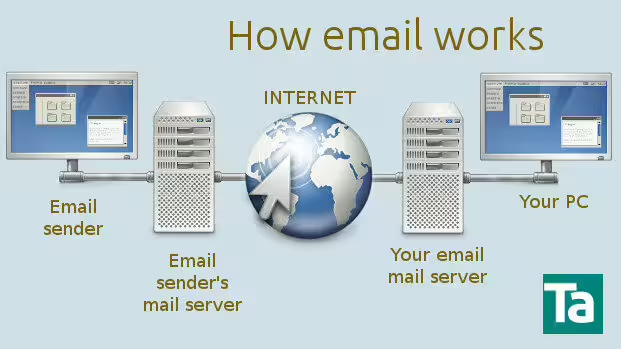
When someone sends you an email your PC or tablet is not connected directly to their computer. Instead your email travels through a linked set of PC and computer routing equipment and the internet.
In its way your email passes through several machines and this gives rise to several vulnerabilities and security issues which you need to consider.
First, the email is encoded and sent up to the sender’s mail server (a specialised computer) which then looks up your mail servers web address based on your email address.
Secondly, it then sends the email to your mail server (where your email account is held – usually an ISP or ADSL provider, gmail or other email hosting company across the internet.
Your mail server will probably make some spam checks on the email and if it fails these then the email may either be bounced back to the original server, or marked as spam and placed in a junk mail folder on the server. This will depend on any filters you have set-up on your email account.
The third stage is for you to read your email – this can usually be done in one of two ways.
(1) Webmail.
Using your web browser (Internet explorer, Firefox, Chrome etc) you go onto the website designated by the email provider – provide your password and email address and read the emails, including any in junk folders.
You can read, delete or whatever on the server.
(2) Email Client
An email client is software on your PC – examples include Outlook Express, Windows Mail, Outlook and Thunderbird. This software needs to be programmed with the address of the mail server, your email address and password – it then carries out your webmail tasks but on your machine.
Because of modern devices like tablets and smart phones you have the option to leave the messages on the mail server so that you can read them on other machines or delete them when read.
This facility was important in the past as mail boxes were relatively small ( a few megabytes of data) and once full refused new emails. Now they are often several gigabytes (a Gb is 1000 times bigger than a Mb) so can store lots of emails and it is reasonable to leave emails for several days so that you can read on other machines if you prefer.
The advantage of the email client is that you can check all your accounts automatically, without the need to log in multiple times – much less work, as multiple email addresses are vital for internet security (see Do not rely on just one email address).
Sending emails is a reverse of this procedure.
Useful tips for security
(1) Passwords
As with all passwords it is important that it is as strong as you can make it and unique (certainly not the same as used for any websites).
If you make the password the same as a website where you use this email account when you join and the account is hacked – they will have your email password too.
(2) Spam and viruses
Most PC virus checkers will also include emails that come in, but never open suspicious attachments.
(3) Checking the email source
As mentioned the mail server will do a series of checks on the email based on content and source and probably tell you its findings in the header.
If you are concerned about an email it is good practice to view ‘The Source’ – how you do this will vary across email clients and webmail (for eample Thunderbird ->View ->Message Source).
This is a good idea if you are unsure if the sender is who they say they are – a particular problem as the mail server can be ‘spoofed’ – it simply passes on the name it is given. I have even received emails purporting to be from my own account.
It will show the routing of the email which may not mean much to you but look out for an entry DKIM and a long key which will indicate the email was ‘signed’ with a private-public key system and very likely to be a genuine email.
In the past I have used this to compare emails from a company which were usually signed and those purporting to come from the company which were not – a good sign of spam.